Recently, I worked on an infected WordPress website, a standard operation that I perform on a lot of sites of all sizes and all over the world.
Shit happens, and a plugin that has not been updated, a theme leftover with a backdoor, a not-well configured website means more opportunities for hackers and bots to infect vulnerable websites.
But this time, something was different. After cleaning the website from both a filesystem point of view and a database overview, I went to check the server config. Even if they didn’t implement a proper configuration and were using some outdated PHP version, the site should work and I should be able to clean it and make it run well.
The necessary extra steps involved to optimize, secure, and harden the site would indeed be needed, but what happened? The site kept on having redirect loops when a call was made to a file… but the file was not there! Imagine this, a call to a URL like:
https://yourwebsite.com/wp-content/themes/yourtheme/assets/myriad-pro/style.cssThe file doesn’t exist, YET the server redirects to a malicious website.
Clearing the cache didn’t work, at least Varnish, Memcached, Opcache, or Redis… plus any local cache plugin like WpRocket and similar.
It was something that occurred at a higher level; it was at Cloudflare’s level (that’s what they used for domain hosting). By checking the URL, I was experiencing redirects and could not easily spot where:
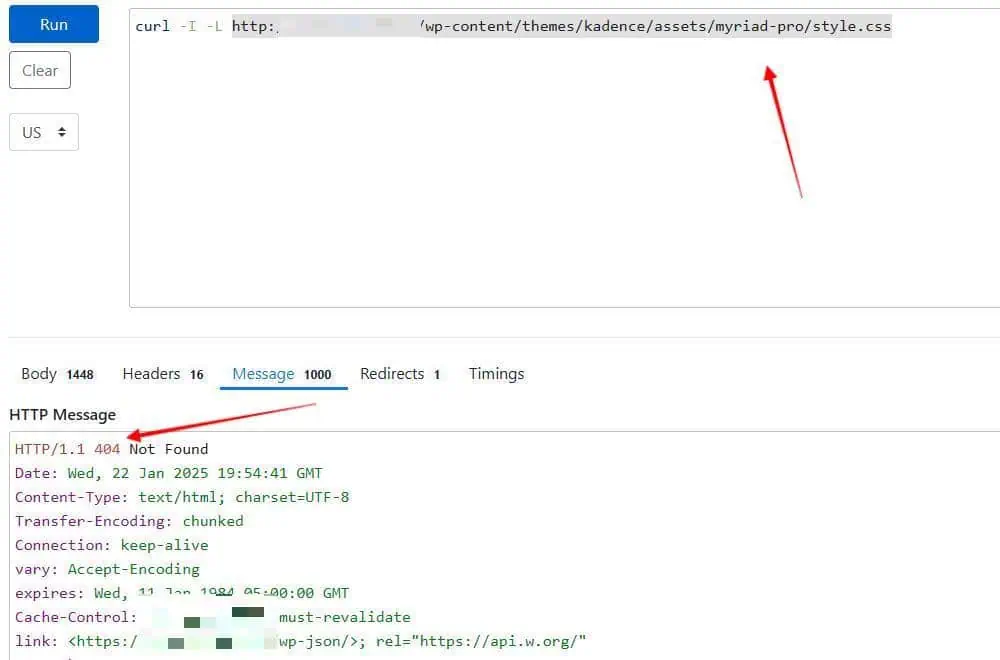
I was able to finally troubleshoot the issue by disabling the proxy on the A record and reloading the redirect URL. I noticed it improved the website’s loading speed significantly. Additionally, I conducted a thorough analysis of the traffic and identified some sources of access that were not optimized.
CACHE POISONING : WHAT IS AND HOW IT WORKS
Cache poisoning occurs when an attacker manipulates a web cache’s stored content, leading users to receive corrupted or malicious data instead of the intended information. This attack exploits the way browsers and proxies save content to optimize loading times, allowing malicious actors to inject harmful scripts or deceptive links into seemingly legitimate pages. As a result, users may unknowingly expose themselves to phishing scams, malware downloads, or false information, jeopardizing their security and privacy.
Combating cache poisoning requires a multifaceted approach. Website administrators must implement proper security measures, including validating user inputs, using HTTPS, and configuring web caches carefully. Regular audits and updates can help identify and rectify vulnerabilities before they are exploited. In an era where misinformation spreads like wildfire, safeguarding against cache poisoning is essential not only for individual users but also for the integrity of the web as a whole. Being proactive in understanding and defending against such threats is crucial for maintaining a safe online ecosystem.
Imagine the horror of clicking on a trusted website only to be confronted with a wall of disinformation, or worse, harmful software that could jeopardize your personal information. Cache poisoning manipulates how browsers store and retrieve web data, allowing cybercriminals to inject their own malicious content into what should be a safe visiting environment. The repercussions extend beyond a tarnished reputation—financial loss, a decline in user trust, and potential legal implications loom large. As an individual, a small business owner, or a web developer, you must grasp the nuances of cache poisoning; the very integrity of your online identity could hinge upon it.
But why does this matter to you personally? Because the ramifications of this threat reach far beyond the realm of cybersecurity professionals; they can affect anyone with an online presence. Whether you operate a blog, run an e-commerce site, or manage a corporate website, the chances of encountering cache poisoning are regrettably high. Cyber-attacks are becoming increasingly sophisticated, and ignorance is not bliss—it is an invitation for disaster. By arming yourself with knowledge and preventative strategies, you can safeguard your content and your audience from the perils of cache poisoning.
ACT PROACTIVELY, DON’T WAIT
In the following sections, we will delve deeper into the mechanics of cache poisoning, unravel its implications, and equip you with actionable steps to both prevent and recover from such an attack. This isn’t just about technology; it’s about empowerment. Knowledge is your best defense, and by understanding cache poisoning, you are taking a proactive step towards fortifying your online websites. To prevent and fix cache poisoning issues on Cloudflare-protected websites, implementing a multi-layered security approach is essential. Start by enabling Cloudflare’s Security Level settings to at least “Medium” and activating the Web Application Firewall (WAF) with appropriate rulesets to filter malicious requests. Additionally, configure strict SSL/TLS settings, ensure that all traffic uses HTTPS, and enable DNSSEC to prevent DNS-based cache poisoning attacks. Regular audits of your cache configuration, including cache-control headers and Edge TTL settings, are crucial to maintain optimal security.
ACTIONABLE STEPS YOU CAN TAKE IMMEDIATELY
For websites already affected by cache poisoning, immediate action is required through Cloudflare’s dashboard. First, perform a complete cache purge to remove all compromised cached content. Then, implement Page Rules with appropriate cache settings and security certificates, ensuring that only legitimate content is cached. Enable Rate Limiting to prevent subsequent poisoning attempts, and utilize Cloudflare’s Enterprise-grade features such as Custom WAF rules and Bot Management if available. Monitor your traffic patterns through Cloudflare Analytics to detect and respond to suspicious activities promptly, and consider implementing Origin Certificate Authentication to ensure that only authorized sources can update your cached content.
Having DevOps skills can indeed be helpful, especially for working on the server to ensure our site runs well and is hardened at the server level too.
This malicious attack can not only compromise your website but also endanger the trust of your audience and the reputation of your brand. By arming yourself with knowledge and taking proactive measures, you can safeguard your digital assets from becoming unwitting accomplices in the spread of misinformation and malware. Don’t wait for a breach to occur; take action now to fortify your online presence.e presence.
Follow These Steps to solve the issue:
- Disable all the caching system
- Fix the website at filesystem and database level
- Test the website and check for redirects (use CURL command to test the malicious url/website)
- Test the website and check in your GSC and using Virustotal
- Clear the Cloudflare Cache and set up proper rules and harden your website
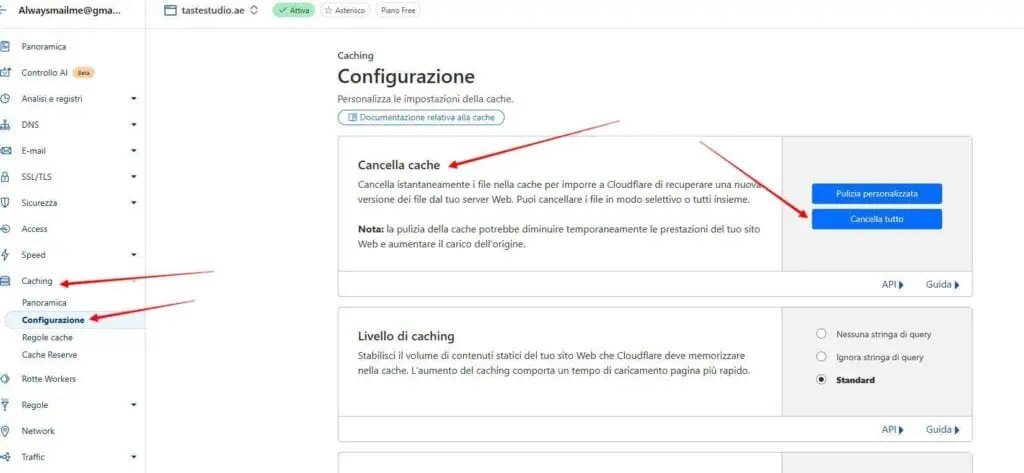
These steps will ensure that your site is safe and clean, allowing you to focus on strengthening and enhancing its security standards. This proactive approach will help defend against potential threats.
If you encounter any problems or issues and need professional assistance, please don’t hesitate to reach out to me for support.