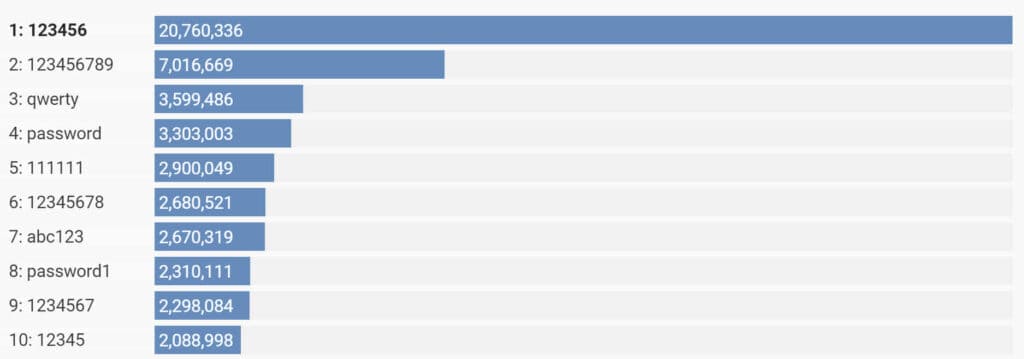
Let’s face it : standard passwords are historically bad but still vastly in use, despite the fact that they are often easy to guess or brute-force. In order to avoid this, people often create difficult-to-remember passwords that are changed regularly. The idea is that if a hacker can’t remember your password, they will be unable to access your account. The use of passwords is, however, not without its merits. They offer a low-cost way for websites to secure their data, especially when the security is only required to be for a short duration or a limited number of uses. If this is not enough….this image shows clearly that a LOT of people are really lazy to deal with passwords, at least in 2018. Until you get burned, probably you will not change your habits, but trust me : you should act NOW.
Why don’t passwords work?
The answer is that the system of passwords has been broken. The password system was created in an era when computers were not connected to the internet and could not be easily hacked. The system of passwords has been broken since the advent of the internet and will continue to break until it is replaced with a more secure system. With advances in technology like 3G, laptops, the internet, and the cloud, security is now a major concern. The use of long and multiple passwords is recommended to make these hacking attempts more difficult, but it really only delays the inevitable. The use of passwords should be limited to where they are the most effective.
The rise in Cybercrime Requires Stronger Security With 2FA

With the rise in cyber-attacks and breaches, you need to make sure you have a strong security protocol in place. The best way to do this is by using two-factor authentication, a procedure that provides a second layer of security to an account. With 2FA, accounts are less vulnerable and it’s more difficult for hackers to gain access.
2FA To The Rescue
To protect themselves, many organizations are adopting two-factor authentication or 2FA. 2FA is a security measure that asks for both a password and another form of authentication before granting access to an account. This typically involves inputting a time-based code, which is sent to the user via SMS or voice call. Other types of 2FA include fingerprints or retina scans. They are an effective security mechanism for protecting your personal information when using online services, because the password is only valid for a single login session, preventing people from stealing it to gain access to your account. The best way to generate a one time password is through an offline token generator or using a service which SMS or WhatsApp you the OTP, but the authenticator app is the better option as, unless your phone is compromised, will run and generate locally the password on the device and then you can use to access the online service it refers to.
Why use two-factor authentication?
Two-factor authentication is a security measure where you are required to have two different sources of credentials, one for your computer and another for your phone. For example, if someone wanted to use your computer to access your account, they would need to have both a password and a code that you could enter on your phone. This way, it is more difficult for someone to steal your password or hack into your account if they have not also stolen or hacked your phone.
Elements of two-factor authentication
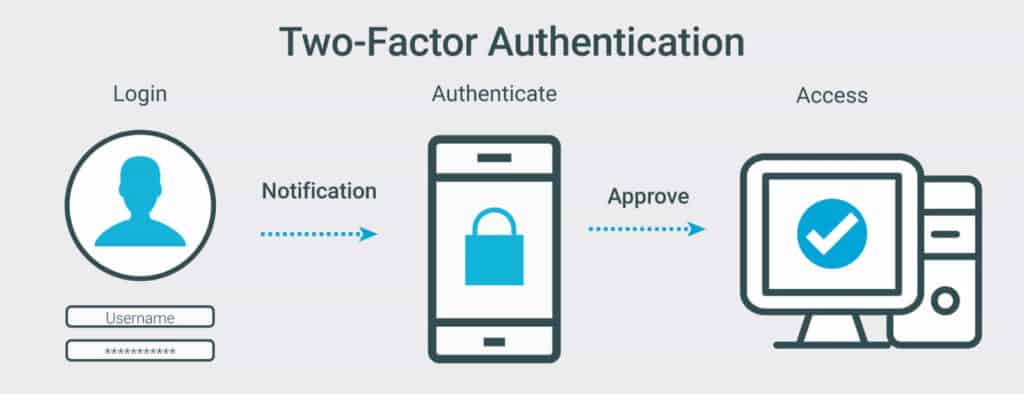
Two-factor authentication is a type of multi-factor authentication that requires the user to have two different things in order to gain access or complete an action. The first factor, something you know, is typically a password and the second factor, something you have, is often a physical device such as an ATM card or smartphone, an auth key generator app or a dongle that will generate the code each time you need a fresh one. Those codes will always change so it will be almost impossible to guess them
The first step in two-factor authentication is to enter your password. The next step is to enter a code from your phone. Third: you’re in!
Common Types of 2FA
SMS authentication
Sms to authenticate are very common and quite safe, the only risk is that, if you lose your cellphone, the account may be compromised since the access is related to the phone number itself. Also if you don’t have a phone connection you will not be able to authenticate since you can’t receive the SMS. It’s a relatively safe 2FA solution.
HARDWARE TOKEN

Using a hardware token is the most secure and effective way to implement 2FA. Unlike the other two methods, this one uses a physical device that has a button that the user must press to validate his/her identity. The device could be a fob, keychain, cell phone, or any other small device which can be carried around easily.
SOFTWARE AUTHENTICATOR APP
Unlike all of the previous implementations of 2FA, this is the most advanced and gaining popularity form of 2FA. It works like this: Users have to install an application on their computer or smartphone, there are various apps like Google Authenticator, Cisco DUO or AUTHY (which I like a lot and use personally) amont others. These softwares dynamically generates 2FA tokens for them that last a brief period of time. After successful login, they simply have to type in on the screen the current 2FA token to gain access to their account. You have also a list of backup codes that you can use in case you have problems logging in and Authy for example works on mobile and desktop PC’s hence you are able to back up your data and settings.
BIOMETRIC 2FA
When it comes to generating 2FA tokens using biometrics, there’s not really an alternative. Your own fingerprint, retina, voice or facial recognition became the 2FA token to claim your identity to get access to your account. While this sound super nice, there are also some fallbacks like a software failure, some data privacy concerns. On the other hand, you can access also it if your mobile is offline and it’s quite secure.
Everybody Should 2FA
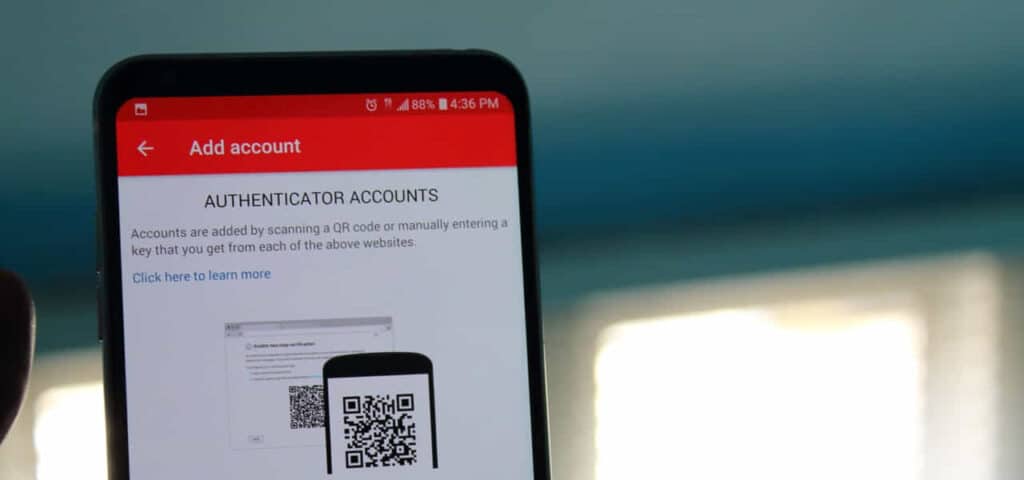
Let’s be clear: Two-factor authentication is not a panacea for Internet security. It does not stop all hacking attempts… but… it makes it much more difficult and time-consuming for would-be hackers. As I already mentioned, If you only have one factor – the password – then it’s easy to be hacked by someone guessing or using social engineering techniques, so adding an extra layer of security will indeed prevent or at least makes it harder to guess such and enter/take control of your personal data.