The COVID-19 has affected and increased scams with more phishing attempts: some data to consider and why you should care for your security
With a lot of people spending more time at home and on the internet and being isolated, phishing scammers found a very big opportunity to hit them. More opportunities and more emails are being sent and received daily, and this gave them a larger audience for ordinary credential-stealing frauds.
Back in April of 2020, Google reported blocking 18 million virus-related scams daily. Google anti-spam filter tho does a great job, estimates suggest it blocks about 99.9 per cent of spam and phishing emails, but these numbers are always changing as tech evolves and scammers always try to find more creative ways to target and cold email potential victims with subtle subjects and content.
from PCMag News
Virus scammers aren’t just going for your passwords; they want your money, stealing an account is not enough, as it will not monetize for them enough well. Scams and cons have been around as long as humanity, and they work online just as well as in person, just use different tactics and techniques. Be very cautious of any email asking you to click a link or download a file or reset a password using their button.
If the fake email’s sense of urgency worries you, go directly to the source rather than using a provided link, what do i mean? Simple: if a DHL email (fake email that seems to be real) ask you to reset for a reason your accounts password, instead of clicking that email uses your standard access website on the DHL website to enter your account and check if there is any sign or request in the page if you are in doubt call the company and ask for clarification. Sadly I had direct experience with some famous companies that as (bad) practice, still send such messages or use email attachments with weird naming, but I will cover this later to suggest a workaround to protect yourself.

What is phishing and how it works and why you must know how to deal with it
Phishing is a type of social engineering where an attacker sends a fraudulent (“spoofed”) message designed to trick a human victim into revealing sensitive information to the attacker or to deploy malicious software on the victim’s infrastructure like ransomware. Phishing attacks have become increasingly sophisticated and often transparently mirror the site being targeted, allowing the attacker to observe everything while the victim is navigating the site, and transverse any additional security boundaries with the victim.[1] As of 2020, phishing is by far the most common attack performed by cyber-criminals, with the FBI‘s Internet Crime Complaint Centre recording over twice as many incidents of phishing than any other type of computer crime.[2]
from WIKIPEDIA
Phishing persuades you to take action that gives a scammer access to your devices, accounts, or personal information by installing malware and collecting data and personal detail through a “fake” website that looks like the “original” one which you use to access a service or application software, but not only in that way.
One of the service i provide to companies and individual is cleaning their website once they have been infected with malware and viruses (check my article here if you’re interested to know more about the subject) , about 60% based on my experience such sites had inside some custom portals that were used to “collect” cards and details from scamming actions. Long story short : the hackers breach into a website, install another “fake” website under a subfolder and when someone click there after being caught in a phishing trap, the site fetch passwords and details as it is styled like the “original” bank, postal, social security or company website!
There are various ways to do so, they could for example pretend to be a person or organization you trust, so they can more easily infect you with malware or steal your information that they can immediately re-use for frauds on other sites.
In other words, these social engineering schemes “bait” you with trust hence the “Phishing” term. This could be anything from a social media log in, to your entire identity via your social security number and in the worst cases can also lead to stealing identity.
These schemes may urge you to open an attachment, follow a link, fill out a form, or reply with personal info, and they will ask to make it as soon as possible as it will create that sense of urgency and warn you. When you see something like that, that’s where you must be on guard and think at least 1 minute before clicking on any element of those emails.
The most common scenarios you will probably face are ones from the below:
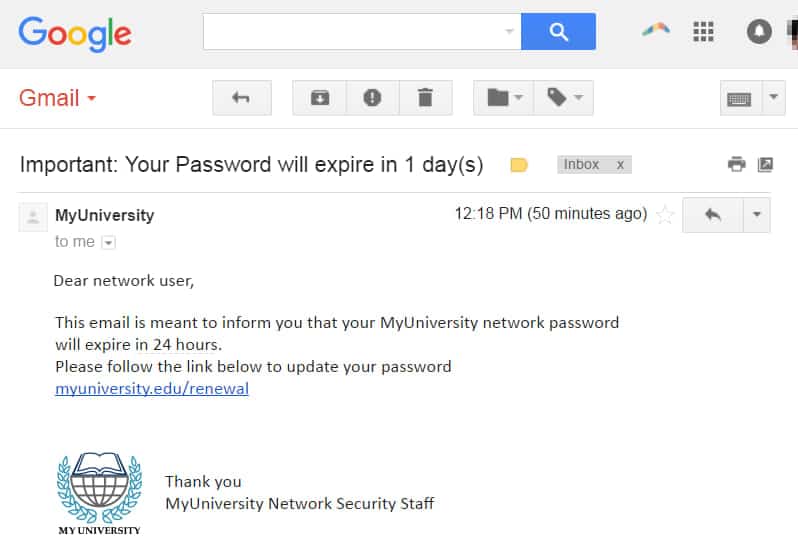
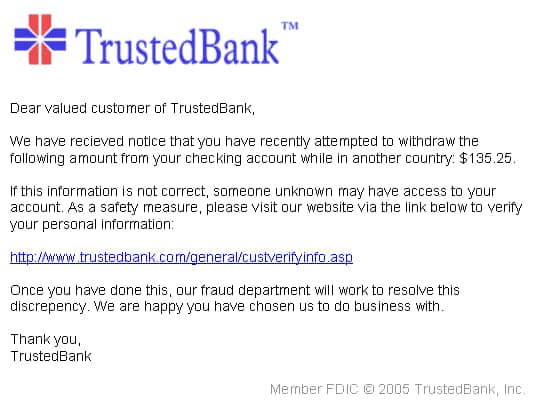
- You open your email and suddenly an alert from your bank appears in your inbox. When you click the link in the email, you are taken to a webpage that looks, more or less, like your bank. And hey, also the links are correct and lead to your “true” bank website. It seems super, I’m safe (they want you to think so!)
- Here’s the catch: this site is actually designed to steal your information and aside from the look, the form and the URL are not right. Probably there will be a message to alert you that says there is a problem with your account and ask you to confirm your login and password urgently.
- After entering your credentials on the page that appears, you are usually sent to the actual institution to enter your information a second time, and this redirects to the “real” website of your bank so you don’t immediately realize your information was stolen. What happened in the background is that your info has been harvested and collected into a file and the scammer now has access to your account or details and, unless there are no other security measures in place (like 2FA or SMS code confirmation or email confirmation to access with SSO, you’re probably in danger)
These threats can get very elaborate and show up in all types of communication, even phone calls that ask you for details or pin codes.
The danger of phishing is that it can deceive anyone and sometimes we’re so busy and overwhelmed with tasks and daily routines that we miss those details.
To help you guard yourself without becoming paranoid, let’s see in detail how phishing attacks work and take it step by step:
- Anyone who uses the internet or phones can be a target for phishing scammers, no exception.
- Infect your device with malware
- Steal your private credentials to get your money or identity or account access to your apps
- Obtain control of your online accounts, the more the better
- Convince you to willingly send money or valuables to regain control of your data
Sometimes these threats don’t stop with just you. If a hacker gets into your email, contact list, or social media, they can spam people you know with phishing messages seemingly from you, as they can probably also get SMTP details, mail passwords and contacts lists. A lot of these cases ends up with people trying to regain back the control of their account ending in a chain reaction where you are just in the middle of the storm. We will see what to do if you think you have fallen into a phishing scam to limit the damages you may have from such happening.

What is Spam and how it’s related to scams and phishing?
Every unwanted email advertisement that you have not explicitly signed up for can be categorized as SPAM or junk email. Spam messages can clutter your inbox and make it more difficult to find the emails you actually want to read, and the more you start to receive spam, the more time you will spend cleaning your mailboxes. Even worse, spam often includes phishing scams and malware, which can pose a serious risk to your computer, so watch out and don’t rush to get rid of these or “consider” them safe. Nowadays tho most email services now include several features to help you protect your inbox from spam and i will highlight some of the most frequently used :
Spam filters
Whenever you receive an email, most email providers will check to see if it’s a real message or spam. Any likely spam messages will be placed in the spam folder so you don’t accidentally open them when checking your email, some of these include SpamCop at the server level or, for example, they can act also at a software level. There is a good list of a few goods and affordable ones here:
https://www.getastra.com/blog/knowledge-base/best-spam-filters-for-emails/
Spam-blocking systems aren’t perfect, though, and there may be times when legitimate emails end up in your spam folder. We recommend checking your spam folder regularly to make sure you aren’t missing any important emails, the initial setup and filtering is crucial to teach these filters how to work and needs to be tuned.
Reducing your spam to avoid Phishing
Here are some more useful tips which can really help to reduce your spam and protect you from phishing:
As a general starter rule set up a private email address, and this email should only be used mostly for personal correspondence and not visible publicly. Because spammers build lists of possible email addresses and often they use tools to guess email by using combinations of obvious names, words and numbers, you should try to make this address difficult for a spammer to guess. Using a simple combination of name+surname is too easy to guess, so try to be creative in that sense adding also numbers for example.
Also, you should protect the address by doing the following:
- Never publish your private email address on publicly accessible online resources, yes, even on your website! You can use forms, responders that hide your email so to reach you a user must fill them.
- If you must publish your private address for privacy terms, try to mask it – in order to avoid having the address picked up by spammers. For example, ‘[email protected]’ is an easy address for spammers to find. Try writing it as ‘Mary-dot-Jane-at-yahoo.com’ instead. I have to be 100% sincere there tho, spammers have apps that can pick addresses easily even in such a way, but at least you can try to be creative and make their life harder!
- Ever tried software called Burnermail? I’ll cover this in another article, cause I simply love it. Basically, it will allow you to create a disposable email that you can redirect to another email, if something goes south you can simply replace it and or change the redirect. In this way, you will know exactly which email has been targeted and compromised and take the right countermeasures.
- Using the burner email as a public email is easy and don’t be afraid to change your public email address often, you can leave it published and it will always redirect and when the old one is compromised you can simply disable it.
- Consider using a number of public addresses. That way you’ll have a better chance of tracing which services may be selling your address to spammers, and this will also give you more options to act in a specific and laser targeted way.
Never respond to any spam. Most spammers verify receipt and log responses. The more you respond, the more spam you’re likely to receive, it’s like a chain reaction, better to cut even before it starts!
You may think: “hey i clicked to unsubscribe so those spam emails will never reach my inbox again!” Well…..when you click ‘unsubscribe’ something happens: Spammers send fake unsubscribe links and emails, in an attempt to collect active email addresses. When and If you click ‘unsubscribe’ in one of these, you just increased the amount of spam you will receive. Do not click on ‘unsubscribe’ links in emails that come from unknown sources.
As a general security measure keep your browser always updated. Make sure that you use the latest version of your web browser and that all the latest Internet security patches have been applied, and once in a while clear your cache.
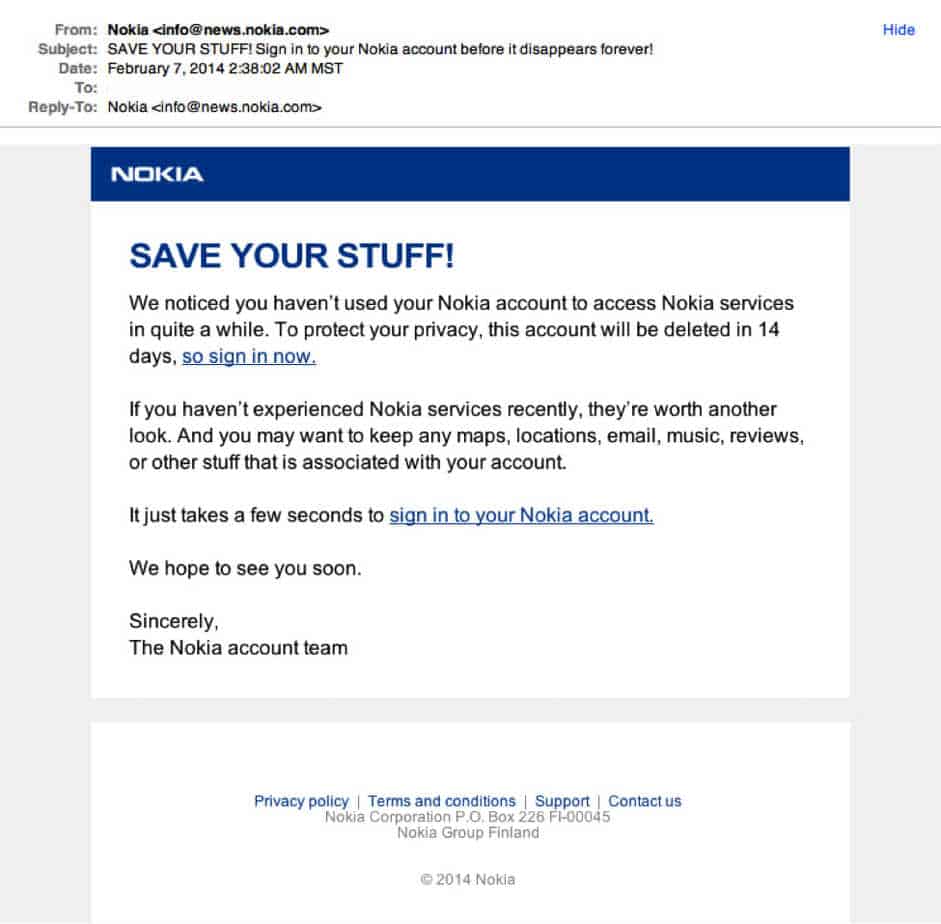
5 Ways to Recognize and spot a fraudulent Email: Real Phishing examples
Phishing is much easier to understand once you’ve seen it in action, and I am sure it already happened a lot to you but you were not aware; it’s not hard, but with these small tips you will know better what to do to identify and avoid them.
Regardless of how they are targeted, phishing attacks take many roads to get to you and most people are likely to experience at least one of these forms of phishing:
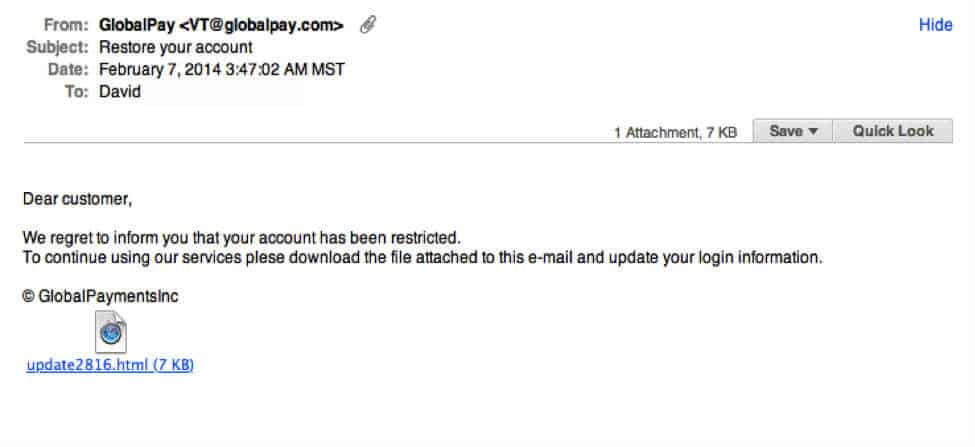
- Phishing email appears in your email inbox — usually with a request to follow a link, send a payment, reply with private info, or open an attachment. The sender’s email might be tailored to closely resemble a valid one and may contain info that feels personal to you so you get trapped and feel confident about it
- Domain spoofing is a popular way an email phisher might mimic valid email addresses. These scams take a real company’s domain (ex: @america.com) and modify it. You might engage with an address like “@arneria.com” and fall victim to the scheme. They sometimes even appear to be sent from the original email address by using advanced engineering so the sender email may be your, but in reality, it’s not!
- Voice phishing (vishing) scammers call you and impersonate a valid person or company to deceive you, usually, this is more complex and I rarely saw this in action but there is still a chance, so better to be prepared. They might redirect you from an automated message and mask their phone number. Vishers will try to keep you on the phone and urge you to take action, so never give them your details or any sensible data, always ask for an email or more details and a number to call back later so you can verify through different channels.
- SMS phishing (smishing) similarly to vishing, this scheme will imitate a valid organization, using urgency in a short text message to fool you. In the message, you’ll usually find a link or a phone number they want you to use. Mobile messaging services are also at risk of this. And in the latest techniques clicking on a link may install malware that can steal data or even send your personal data from your cellphone to another location so NEVER EVER click on links that you receive through SMS or WhatsApp messages unless you know exactly what is the source and what are you doing.
- Social media phishing involves criminals using posts or direct messages to persuade you into a trap. Some are blatant like free giveaways or sketchy “official” organization pages with an urgent request. Others might impersonate your friends or build a relationship with you long-term before ‘attacking’ to seal the deal. If you got a friend on Facebook that seems to have another profile and he asks for again friendship, before accepting, something maybe not be right and the scammer probably is trying to take some action against the original profile owner, verify with your friend or try to reach to the other profile.
What happens if you click a link in a phishing email?
Clicking on a phishing link or opening an attachment in one of these messages may install malware, like viruses, spyware or ransomware, on your device. This is all done behind the scenes, so it is undetectable to the average user. Once the malware has been installed, it could harvest your sensitive information, send out more scam emails to contacts in your address book or provide a scammer with remote access to your device.
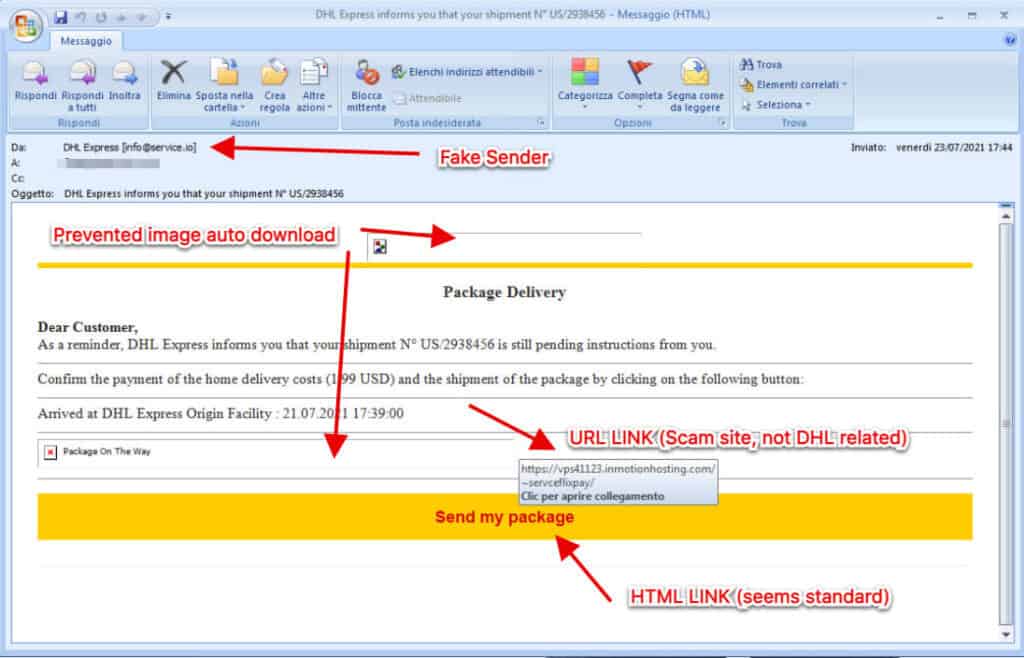
Opening a link will redirect to a fraudulent website that often has been hacked and it’s being used (and abused) to collect data. It’s always a good practice to check the links that are present in the email and the URL. If you have a link for example from DHL which redirects to DHL.COM it may be legit, still, I will not use that link to reset a password or to enter detail.
But what if the link redirects to DHLACC54.XYZ.CN instead but it’s masked as a DHL.COM link? Remember that a link is made of different elements in HTML, I will try to make it super simple. Every web page and every link you see are coded.
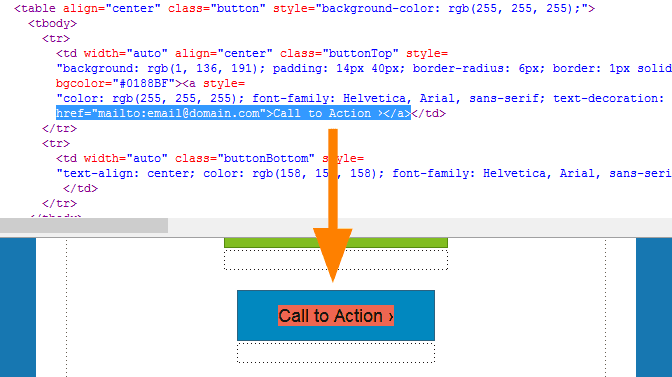
The Links in HTML coding language (that is one of the markup languages used to render items on the web) appear like this :
<a href=”https://myscamsitelink.com”>Link to my website</a> but you will only see (if the email format is HTML) -> Like this for example Link to my website
As you can see tho this can be tricky. You can always right-click and copy the link without opening it, then pasting in a notepad empty file and see where it leads to.
What do you do if you suspect you’ve been phished?
So you’ve been phished, what now?
- Change all your passwords for the accounts that have been compromised as well as the accounts that use the same or similar passwords to those that have been captured by the hacker. It’s quite common that people use the same pass over and over to avoid forgetting it….and once somone guess one…has them all!
- If you entered your credit card information on the phishing page, cancel your card or block it immediately.
- Delete your email account to avoid spreading phishing links to your contact lists unless it’s linked to other services, in such case reach to them asking to change to another one that in the meantime you will have created.
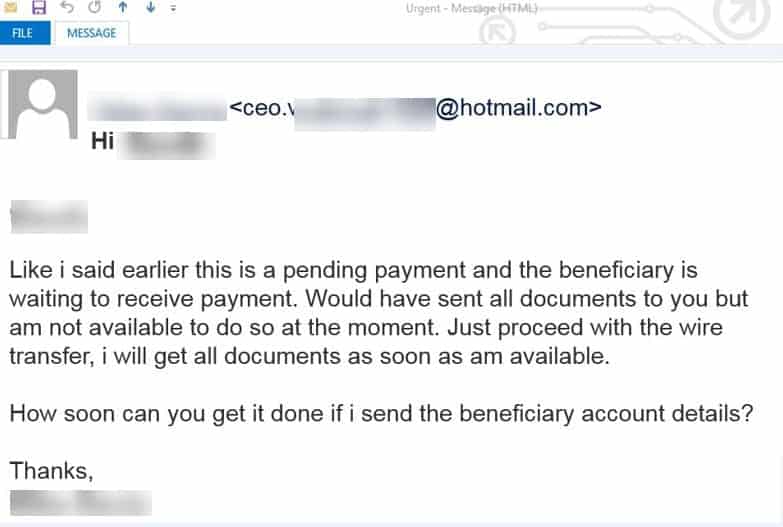
- Contact the company or person that was spoofed – it might be your CEO or it might be a friend or it could be a major company or bank and investigate to make sure this is the case.
- Scan your device for viruses – clicking malicious links can instigate silent downloads of malware that go to work corrupting devices without your knowledge, for example, you may have opened an attachment that installed a trojan and a backdoor that while you work, transfer data and access your details.
TIME FOR THE ACTION – START TO PROTECT YOURSELF NOW!
Phishing prevention tips
Whether we like it or expect it, you will be the target of these phishing emails every day.
Most of these are filtered out automatically by our email providers, and for the most part, users have gotten relatively good at identifying these types of emails and using common sense to not comply with their requests, a lot of the scammers use email warmers, write with good copy and try to even match your “needs” in terms of what you may be interested into. For example, if you have a sports shop a spam email may contain something related to your sports industry type.
You know already how deceptive phishing can be and phishing attacks extend into all types of communication and internet browsing — not just emails.
Beyond spotting the email and removing it, you can guard yourself with a few extra tips. and the more email you start to process and identify, the better you will become to avoid problems. Let’s start with some general rules, and then move to the big 9 for a complete guide.
General Tips for handling known Phishing Emails
Being vigilant about spotting phishing emails is key and it has to become a daily habit. If you’ve come across one in your inbox (that hasn’t been auto filtered into spam), use these strategies to avoid becoming a victim of a phishing attack and detect it.
- Delete the email without opening it. Most viruses activate when you open an attachment or click a link within an email. But some email clients allow scripting, which makes it possible to get a virus simply by opening a suspicious-looking email. Making it best to avoid opening them all together. Some email clients allow a preview panel, like outlook, my advice is to disable that view so you can already have a layer of protection from scripting.
- Manually block the sender adding him to the spam list. If your email client allows you to manually create a block, you should do so. You can also potentially block the domain, but be very careful with this setting.
- If you are being heavily affected by Spam, consider an extra line of security. You can never be too safe. Consider purchasing antivirus software that has as a feature the option to monitor your email box.
9 Steps to protect yourself from Phishing
Internet protection starts with your mindset and behaviour toward potential cyber threats, you have to always be ready to verify the information but be safe when you do so. The best way to handle a phishing email is to block or delete it immediately. Whether you take any additional actions to limit your exposure to these attacks is key.
Here are a few basic measures to always take with your emails and other communications:
- Employ common sense before handing over sensitive information. When you get an alert from your bank or other major institution, never click the link in the email. Instead, open your browser window and type the address directly into the URL field so you can make sure the site is real. It’s very unusual (nowadays i would say impossible) that any bank or company will ask your personal details to be confirmed or sent by email. Watch out for the links, they are the majority of scam gates.
- Never trust alarming messages. Most reputable companies will not request personally identifiable information or account details, via email. This includes your bank, insurance company, and any company you do business with. Creating urgency or FOMO (fear of missing out) is a trap.
- Do not open attachments in these suspicious or strange emails — especially Word, Excel, PowerPoint or PDF attachments. NEVER open them. What I usually do when I am insecure, I save the attachment (and it’s still a risk here) and upload it to a file conversion service, then try to convert it to a jpg file. Recently I had an email from DHL willing that seemed a scam but was legit. As crazy as it may seem, they still have big flaws in their communication email system procedures. Note that when uploading to the server you are still risking as the file may be infected, so watch out. I would never open a file on my computer unless I am 100% sure of it, and taking an extra step is always a good choice.
- Avoid clicking embedded links in emails at all times, because these can be seeded with malware. Be cautious when receiving messages from vendors or third parties; never click on embedded URLs in the original message.
- Keep your software and operating system up to date. Older OS, unfortunately, don’t get security updates and still a lot of companies use them for various reason (for example old machines like plotters or printers may have not a driver for new os hence people still run them on older OS-based pc)
- Reduce your spam following my previous advice
- Check the Address: source, sender and URLs always by copy and pasting to an empty text file to verify what’s happening, also ALWAYS check the URL in the address bar (if you clicked…..you already made a mistake…..)
- Spam messages often contain images that the sender can track. When you open the email, the images will load and the spammer will be able to tell if your email works, which could result in even more spam. You have been tracked! You can avoid this by turning off email images. Depending on your client or services you can control this setting and enable or disable it based on your needs, that’s also why often you don’t see correctly the images in newsletter email, but it’s always better to enable and whitelist the sender than getting tracked
- Report: if the email is hammered from the same sender and it’s present a link to unsubscribe or if there is a REPORT SPAM link in the email message I suggest you not trigger it by clicking on it. Instead, go to the sender page and fill a Spam Report form. A lot of services are very very strict with spam reports (as it will hit their sender IP’s reputation so they will act to keep it clean, and can potentially and often also disable the sender account). Usually, this is more related to email newsletters services (like Mailchimp, Sendinblue, Moosend etc.) tho, so I would say that phishing emails are not the type that you can, unfortunately, report at this level.