- Goal: Quickly and effectively restore a hacked/hacked / malware-infected website
- Difficulty level: variable, intermediate-Advanced depending on the type of malware
- Required skills: basic PHP, FTP, use of the control panel of your hosting
- Intervention time: variable according to the level of severity and degree of penetration, from a minimum of 1 hour
1 -BACKUP: RESTORE OR PRE-INTERVENTION EXECUTION
If you have a clean backup, don’t think twice and restore it. It will allow you to quickly return to the state your site was in before being attacked and then work on security or updates to prevent it. It’s like using a time machine, and I assure you that no matter how trivial my suggestion may seem, it is something that is often ignored, perhaps taken by the anxiety of the moment and the rush to “fix things”.
Don’t be one of those users who thinks “oh well, if it happens to me I’ll put it back to the beginning”. In fact, with regular backups, you can get rid of a lot of problems. But be careful: don’t believe that your hosting must necessarily think about having backups even if that’s what they advertise in their splendid marketing campaigns. The only (safe) way is to make sure by asking them and then, in addition to their backups, use an ad hoc solution for WordPress that can make incremental or full backups depending on your settings. & Nbsp;
Obviously, if your site has data relating to customers, orders or other information that could be changed and therefore would be lost by restoring it, I recommend that you make a backup of the “hacked” site or save these info if they are stored under form of files. In the first case you can perhaps install the database locally on a clean installation and extract the data that you will then re-import into the site, in the second you just need to upload the documents once the site has been restored to its optimal state.
If you don’t have a backup, make one via your server control panel or manually download the site and make a database backup. It doesn’t matter if the site is compromised, it is data that you may have to recover anyway and it is a good idea to keep it safe.
2 IDENTIFY THE ORIGINS AND CAUSE OF THE INFECTION
First check the activity logs on your server and FTP, accesses, errors and anything else available.
90% of the site was infected through a plugin or an outdated / secure theme, or for example the code of a previous unused wordpress installation and not deleted from the server or an inactive staging copy but still present (very bad habit, you must always leave it clean !!)
But there is also one last (alas!) possibility, which I have encountered several times: shared hosting without separation. What does that mean?
Simple: all the sites are present in the root (main directory) of the site and each has its own folder …. but they are all accessible from the root. Perfect, this, for a malware, which in fact, in addition to infecting a site, will communicate with all the others, creating a real chain reaction that will pierce / hack all the sites on the server. Bingo !! With a single blow it knocks down even fifty! Well, now you know what to ask of your trusted hosting: separate environments, even if on shared hosting. Thank you.
3 UNDERSTAND HOW THE VIRUS WORKS AND READ THE CODE
First of all it must be said that when a site is hacked you realize it because in addition to not working well, it presents several problems. For example, when you visit the pages you are redirected to external sites without your being aware of them or third-party content appears or you receive download messages such as files that could infect (in addition to the site) even your beloved PC. To do this, hackers usually insert malicious code into website themes, plugins or CORE files. At best. In the worst case, they also access the database. But what is a VIRUS? It is a script, of the code that is executed and that performs chain operations at the moment in which it finds certain conditions. For example, a virus can cause each file with the .js extension (javascript) to be renamed and added a code that makes it illegible or blocks its functionality
🧰 WHAT ARE THE TOOLS I RECOMMEND TO USE
In order to find and “clean up” the site, we need to know how to work with the code. Knowing how to use a web code editor such as VS CODE, SUBLIME TEXT, BRACKETS, NOTEPAD ++ etc.
- Also, you will need to know how to access your site via an FTP client, I recommend FILEZILLA , free, updated and always lightweight.
- Knowing PHP as a language, at least at a basic level, takes about a couple of hours, and allows you to have some rudiments to understand what to delete and what not.
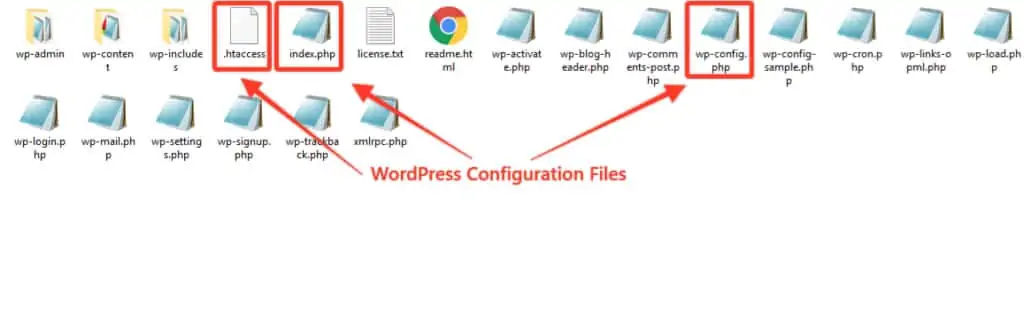
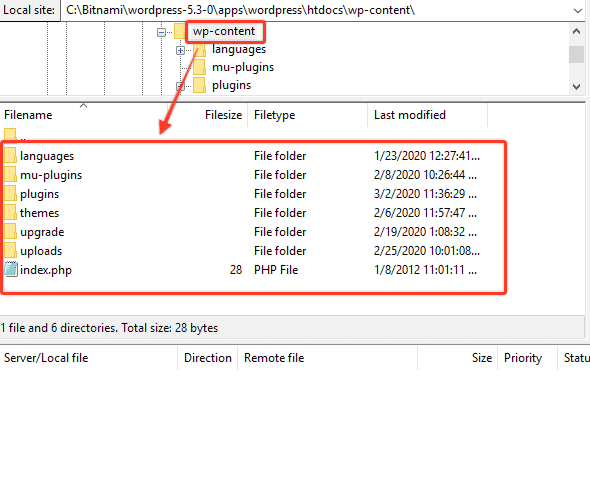
- In order to find the infection, you need to check the files on the site. If you have never worked with WordPress, do not panic, the structure is very simple and tidy.
- Download WordPress from the official site on your PC to be able to “see” and have at hand a clean structure to compare. I show you in the images below some details such as configuration files and directories.
- In a “compromised” WordPress site you will find, in addition to other files with names that are nothing short of “unusual” or without extensions, also some “original” files that are modified with malicious code.
💡 TIP Before deleting the “doubtful” files, I advise you to rename them by changing their extension Eg. Asdadsg.php to asdasdg.php_SUSPECT (added an underscore and renamed)
- In this way in addition to “inactivate,” you can always rename it where you made a mistake
- download the suspicious files on your PC in a dedicated folder.
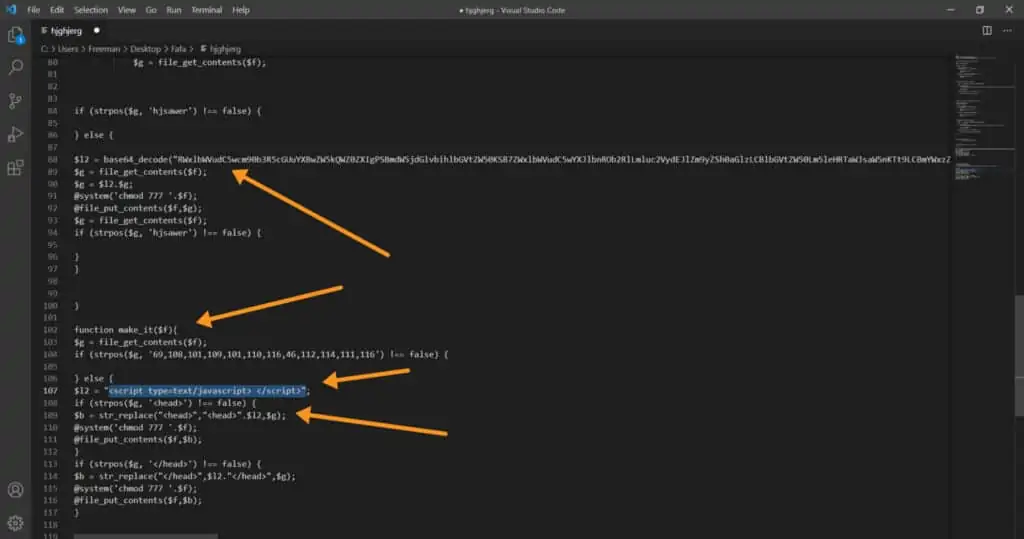
At this point, open the offending files and read what’s inside, if it is a virus you will notice it as in addition to not having a code formatted in an orderly and commented way, has functions that inject malicious code into the site. Below you will find an example of this.
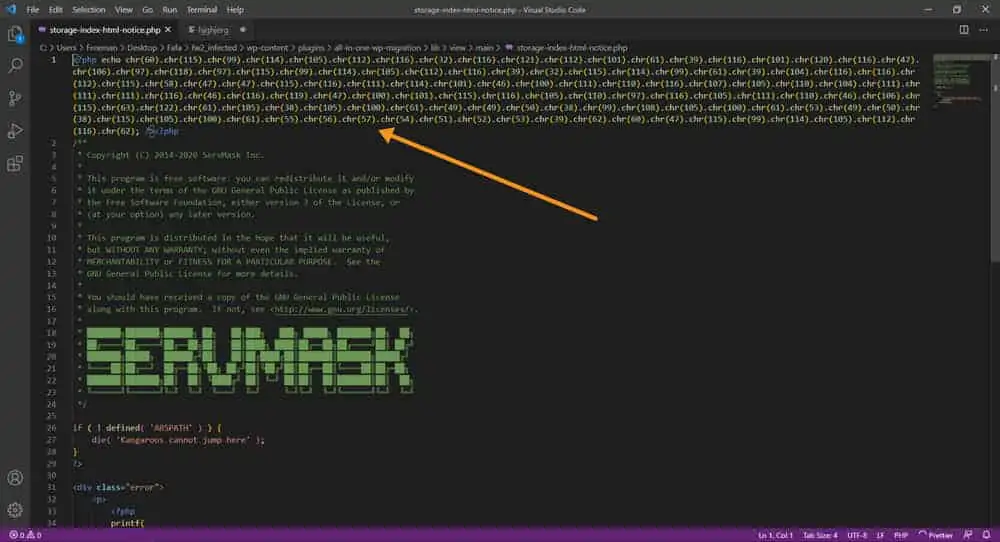
💡 TIP I give you some clues, often recurring in malware. The functions below in fact allow this code to replicate itself and inoculate the malware on your server and by looking for them you can save time:
- base64_decode
- is_admin
- eval
- gzuncompress
- passthru
- exec
- shell_exec
- assert
- str_rot13
- system
- phpinfo
- chmod
- fopen
- fclose
- readfile
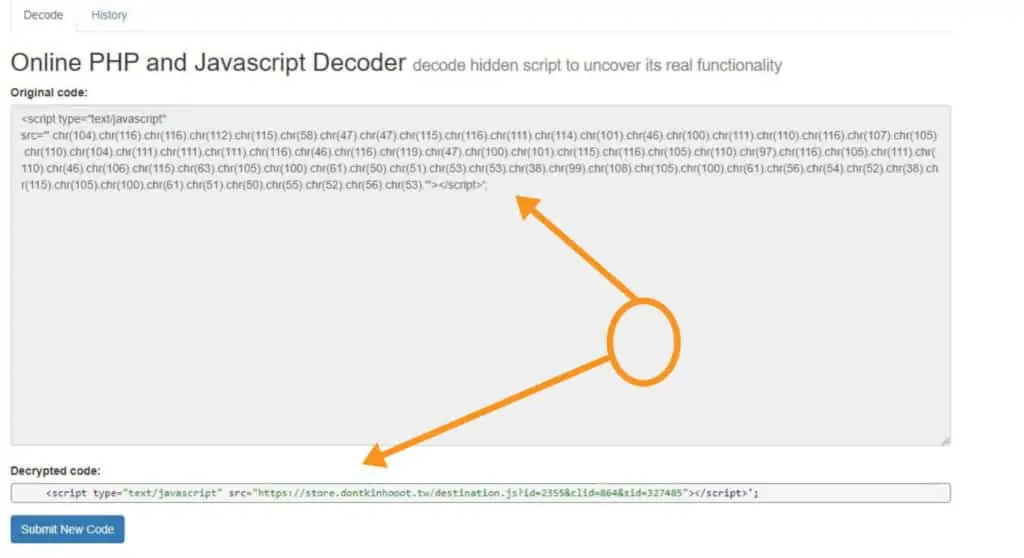
💡 TIP Did you find an illegible alphanumeric code? Do you want to know what this means?
If it is encoded with a base_64 system then copy and paste it here:
🚀 Base64 Decoder https://www.base64decode.org /
And you can see what the virus “inoculates” in code terms.
Another gem? Want to know what all that code you see “before” your classic files means?
🚀Malware Decoder https://malwaredecoder.com/
Copy and paste here ….. SURPRISE! That code is automatically converted into a script that is inserted and executed on your pages ….. Didn’t you expect the malware to be “plain” or “visible” just by entering the site name?
💡 TIP : ideally it would be great to have a “monitor” that shows you the permissions changes or file changes on the server by date, this way you could save even more time in the search!
4 – MALWARE REMOVAL AND RE-UPLOAD
Now that you know how malware works, and once you’ve found some “malicious” code, you can download the site en masse (you can often even “zip” it from your hosting panel) and use a tool to start ” compare “your directories with the” standard “ones of a clean WordPress installation. Some tools that can help you with this are:
👉 Beyond Compare (commercial, but really powerful)
👉 Meld
Once you have chosen the tool, you just have to compare the files in search of the malware code and the “suspicious” files to delete.
After cleaning you can upload the correct files to your site and test the site.
Is your site still not working? Are you sure you have checked the site thoroughly? Give it another try!
Often, malware is “content” to hack the site and work at the file-system level, but if not, then get ready ….. a tutorial will not be enough as they may have infected the server at a higher level as well. deep or the database.
If you still have problems with the site contact me, I will help you in a professional and quick way to restore and “clean” infected websites. you will pay nothing. Either I solve, or nothing!
5- SECURITY OF WP AND CONTROL ON GOOGLE SEARCH TO AVOID SEO PENALTIES
A few steps now that the site has been cleaned up are needed to prevent it from being re-infected.
- Change database logins and passwords of admin profiles
- Change and regenerate wordpress SALT KEYS of the new ones that will “cut” any tunnels left open by the hacker’s sessions)
- Ask for a restore of permissions for dir and files to your hosting, in fact, often the malware modifies to permission chmod 777 (readable, modifiable and executable files from the WORLD!) to then be able to modify the files and make a better hole in the site again. htaccess and wp-config which are, among other things, very important and it is also through these files that you can add directives to your PHP server too so watch them out carefully!
- Enter your site and check that all plugins are correctly updated to the latest versions and remove unused or obsolete plugins (REMOVE, DO NOT DEACTIVATE!)
- IMPORTANT – If your site has been marked as Infected with Malware it is likely that Google will report it as such and therefore penalize visits with a warning. If you have cleaned the site you can request a verification which usually in 24 hours or less will allow you to “unlock” the status and re-index it positively.
💡 TIP: Malware often creates directories in the plugins subdir which are not visible from the admin side, keep your eyes open! Same goes for the dir MU-PLUGINS (Must use plugins)
⭐ RECOMMENDED BACKUP TOOLS
Of course if you had baclup you wouldn’t have had to read this whole article and spend hours of your time, and money. A little patience, a few clicks and that’s it!
Don’t worry, it happened to everyone. Even worse than this!
But let’s make sure it doesn’t happen again! Consider having regular backups using a specific tool at certain times.
A plan of action could be to set up bi-weekly backups and download them monthly if you prefer to your local drive, as well as keep a copy in the cloud. In this way you will have a “double” action plan that you can activate if the need arises.
Personally, I recommend these two WordPress plugins that I would recommend:
🚀 WP VIVID
It offers several features including support for large databases, site migration and automatic backups as well as export to external clouds as well as to a local server. It supports incremental backups and much more. It allows you to divide the backup into various files for better management and other interesting features etc.
⭐TRUMENTS RECOMMENDED FOR THE SECURITY OF THE SITE
Finally, I would like to recommend to you some tools that are Firewalls and Anti-Viruses that can be installed on your sites with a few simple steps and can help you in semi-automatic or fully automatic cleaning.
Personally, even if I have the skills to work manually, I use also some softwares when I want to have a double confirmation of the work done or even just in fast pro-active on the sites of my customers that I manage from a security point of view.
In many cases, in addition to offering real-time protection, they are able to block the spread of malware.
It must be said that sometimes they do not succeed immediately (it happened to me with a new 0 day malware that I cleaned it before I recognized it), but maybe after 24-48 hours and if the site has been deleted, for example, they won’t be able to do much, but they can be set up to act more or less “hard”.
Obviously these are tools that must be configured, and which initially can give false positives or block the communication of the site with third party services, just like a real FIREWALL. But with a little bit of tuning and tuning they will work better and better over time.
If time is money for you, opt for professional advice, if you can wait then consider it, it is money well spent and put it in the budget. Contact me, I will help you professionally and quickly to restore and “clean” infected websites. And if I can’t, you won’t pay anything. Either I solve, or nothing! I can also do a security audit of your site or an optimization, as I said, prevention is always better than cure!
Furthermore, with the exception of Malcare and Wordfence, Astra and Virusdie can also be implemented on other frameworks/sites, not only on WordPress.
👉 VIRUSDIE
👉 WORDFENCE FOR WORDPRESS SECURITY ⭐ (My Favorite for WP)
👉 MALCARE